March, 20th 2018
Using mobile hotspot with mobile operator that restricts tethering
Time-to-live
The main method for mobile operator to check if your are using other devices through mobile hotspot is TTL value of network packet. Every network packet has a number TTL (time-to-live) value and it decrements every time packet goes through router.
When I'm using my iPhone with "Yota" packets that come from my device have TTL value of 64. So the provider expects all the packets to come with 64 value. If I'll connect my MacBook to iPhone hotspot and make any request, my iPhone "router" will substract 1 from 64. This way Yota will block every request I make from my MacBook connected to iPhone hotspot.
The good thing is that we can manually set TTL value for all requests coming from MacBook in terminal by running this command:
/* shell */
# Note: configuration will reset after system reload.
sudo sysctl -w net.inet.ip.ttl=65This will set TTL to 65 and after going through iPhone "router" it will decrement to 64. Yota won't detect tethering!
One more thing
Unfortunatly, that's not the end. Providers usually scan traffic and monitoring what endpoints you are requesting to. In particulary, provider detects that if your iPhone is sending the requests to Mac OS update server, then it's obvious you're on mobile hotspot with your MacBook.
I also found that while using some of default Mac OS apps like Mail, Notes, iMessage and FaceTime, iTunes and other, Yota starts blocking you connection. Moreover Mac OS is sending some system requests in background, so in this case you can't just quit the app.
Here LittleSnitch comes to help.
Configuration
Little Snitch is managing all you system connections the way you want it. You can create quite flexible set of rules and profiles.
To be sure the system is not making request you don't control lets create new separate profile:
Then add rules to disallow all incoming and outgoing connections and rules that allow connections from apps that you need.
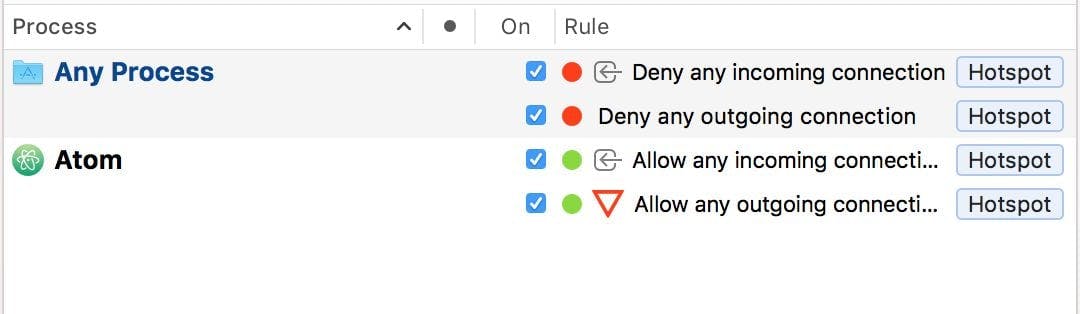
That way all connections that are not explicitly allowed, are blocked.